Inside the DPRK Fake IT Workers Network: IP Ranges, Proxies, and Internal Coordination
Inside the DPRK Fake IT Workers Network: IP Ranges, Proxies, and Internal Coordination

Summary
Following a compilation of mail republished by @Sttyk we used Hudson rock to legitimate the data provided in this mail dump and found many artifacts that belong to DPRK IT Workers. In this article we will focus on a reconstituted infrastructure and the environment of this structure.
Mapping their Internal Infrastructure
During our investigation we found that they use “IP-msg” or IP messenger an app used widely inside of their infrastructure to communicate between different teams, with that data, we added more context to our first finding where we only had local IPs.
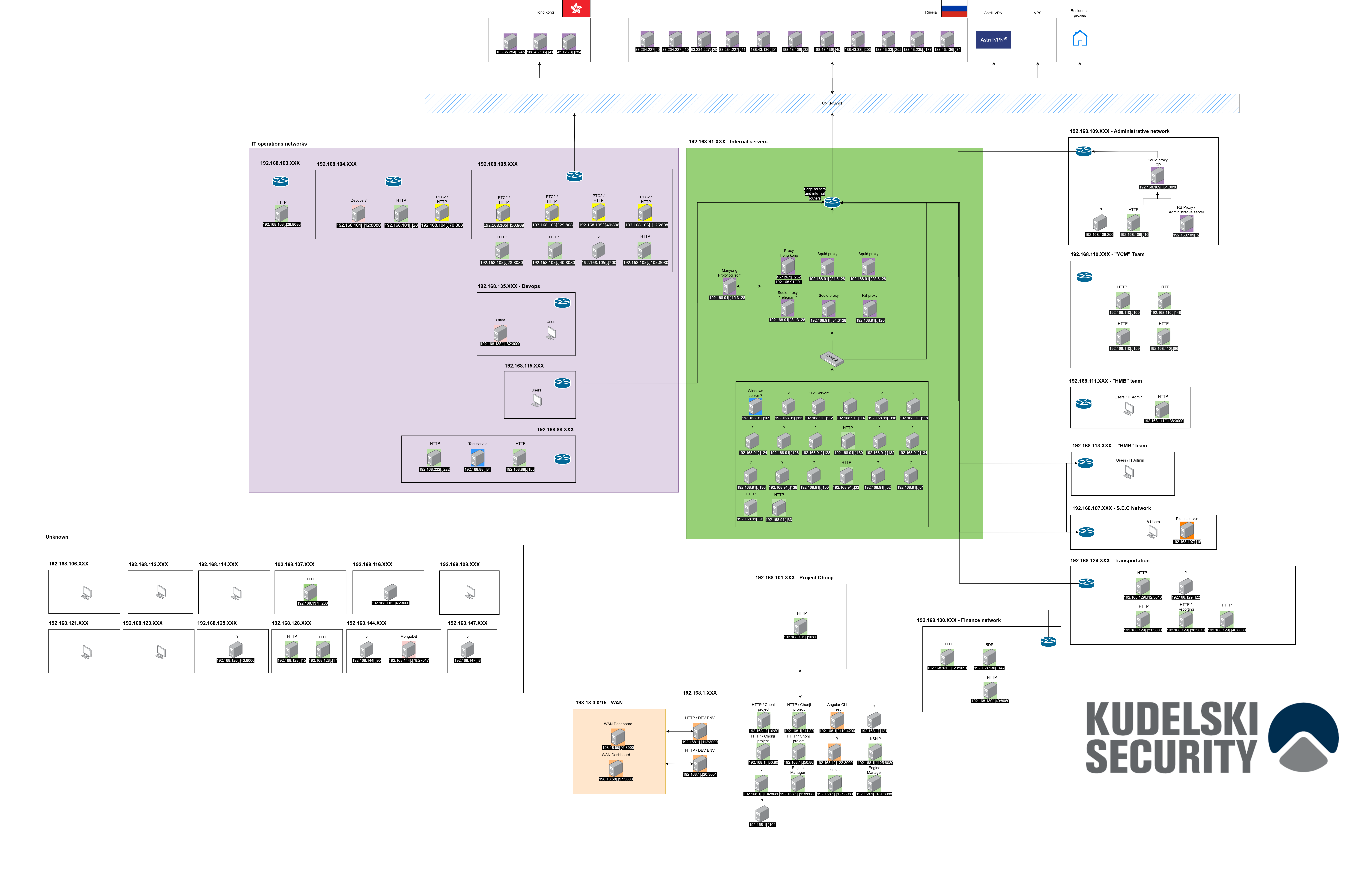
It seems that they have a single unified network for everyone working as a foreign worker.
As noticed by NKinternet we mainly saw these ranges being used among IT workers, the ranges 188.43.88.0/24 ; 188.43.136.0/24 ; 83.234.227.0/24 are also used by many companies not related with North Korea at the time we are looking at these ranges.
In Russia we can say with moderate confidence that they contain both residential IP’s and Proxies because some IP addresses are related to legitimate companies, most of which are transport companies.
As found by NKinternet the note below gives us more context on the purpose of these public IP addresses.
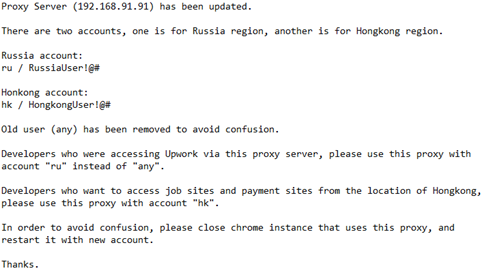
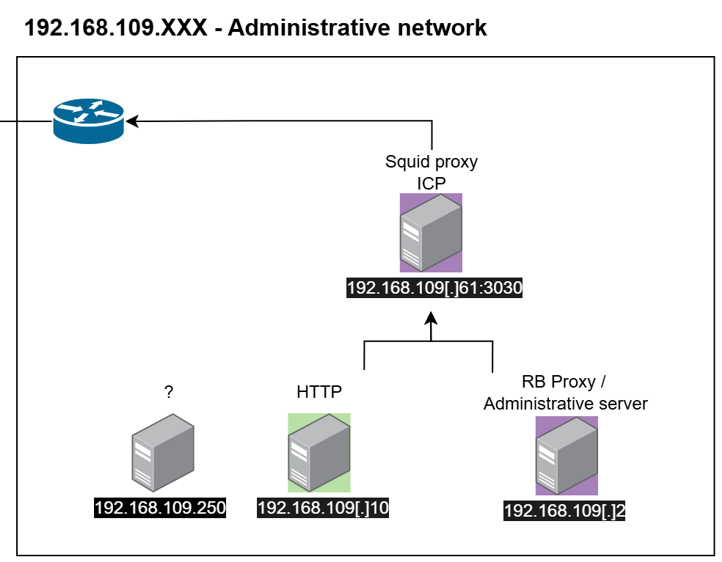
From this note we pivoted with the password of the Hong Kong proxy provided and we found a private IP address linked to the network 192.168.91.XXX where we can find most proxies and servers.
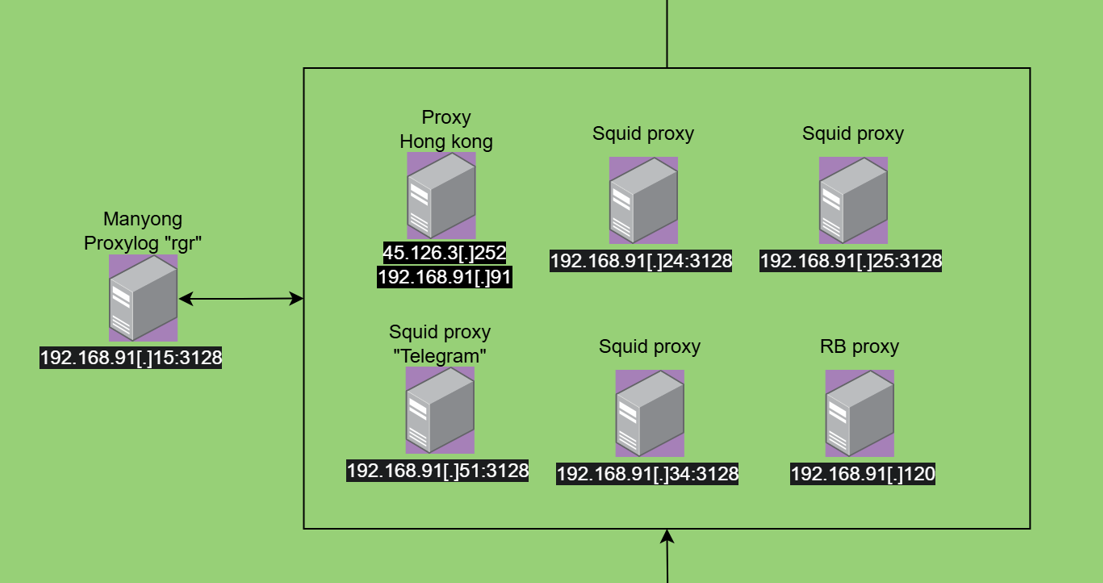
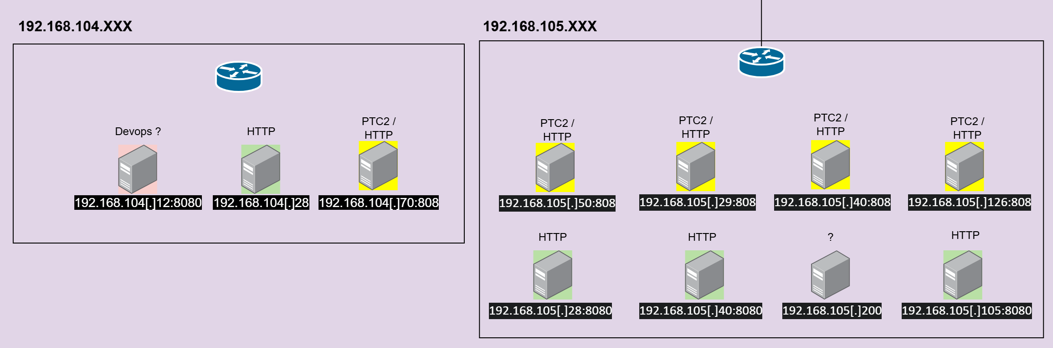
We can note the usage of squid proxy by the port used “3128” and we can say with low confidence that unauthorized access are logged on the “rgr” log aggregator. Each proxy is used for different purposes for example 192.168.91[.]51:3128 is used to redirect telegram requests according to a “smart proxy” configuration file found on Hudson rock, there is another pool of proxy servers identified as “PTC2” on the port 808 these servers has been found on some IT workers web browser and saved credentials which is also used for their browsing, while we don’t understand the choice of getting multiple types of proxies to do the same thing which is redirecting the browsing traffic.
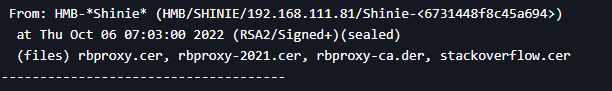
The mention “RB” which is a proxy as we can see on the chat logs has been mentioned on a message from “Victory” that we attribute as an IT administrator.
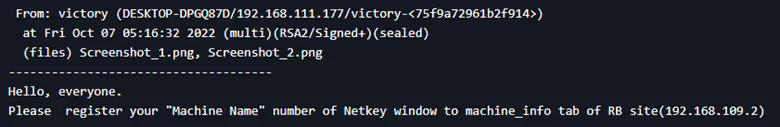
According to the urls accessed by the local users and the message from the IT administrator we can say that this specific server expose the port 80 to facilitate some internal tasks.
Inside this server they must indicate the following information:
“email” = A mail
“identifier” = A mail
“birth” = birth date
“Machine info” = Product key windows
“team” = It might be composed with [Department number + team number] [example 821-39]
“Username” = Internal name
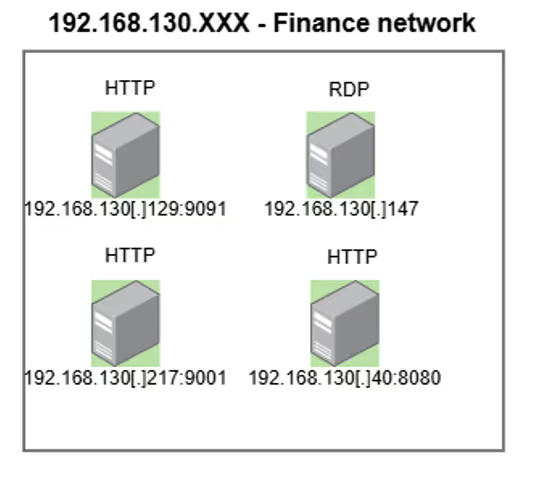
“UserID” = ID declared on this serverTo coordinate all this workforce they have a centralized way to report such as the financial network segment that we can attribute by the name of the URLs visited found on their browser history. We noticed the usage of the same type of servers on other part of the infrastructure which seems to be for reporting purposes of their activities.
Internal Chats
By using only the stealer logs pulled we were able to find chat logs from IP messenger, a software widely used among North Korean people.
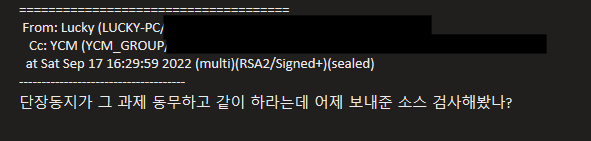
Translation:
"Comrade Director says to work on that project together with [that] comrade. Have you reviewed the source code sent yesterday?"
With these chats we can see patterns such as north Korean patterns of languages such as “Comrade”, “Comrade + name, Comrade + function with an authoritative way to talk. It seems that not all chats are like that, North Korean IT workers switched to English surely to improve their skills because they need to improve their English to speak fluently during their job interview.
As the DPRK fake IT workers speak many languages mainly English, Korean, Chinese, Russian and Japanese it’s hard to know if they have access to the infrastructure remotely with a VPN or if they are all in the same place, we can say with low confidence that some employees have a remote access to this infrastructure based on diverse time zones set on their computer that can be also used to only look at the time easily to their target country, their google history to convert “myr” (Malaysia), “sgd” (Singapore), ”lpa” (India),“rmb” (China) currencies to USD See [Annex 1] and their travel to the same countries cited before.
Cholima group shared a chat log that we were not able to retrieve on their blog, it has been reshared by @Sttyk on X as a screenshot that we crossed with the report of MSMT. By adding the data of the screenshot and the data of the chat gathered on Hudson rock we were able to identify a few entities of the UN designated entities, please refer also to [Annex 3].
Here is a table of identified acronym with moderate confidence.
Source
Hudson rock (for the stealer logs)
Recorded future platform (for the confirmation of residential proxies)
https://x.com/SttyK/status/1997411128897646988 (for the naming conventions see Annex 3)
Annex 1
Annex 2
Annex 3
[Department + Team number ]
Letters can be only the team without the number or a company acronym












































.avif)




.avif)














.webp)
