Blackbasta Alert – Action for CISOs
Blackbasta Alert – Action for CISOs
Operating SOCKS proxy
We observed them managing at least one SOCKS proxy server that is publicly listed. Although we couldn’t verify it, we suspect these servers are utilized for credential harvesting or malware injection. This inquiry is currently underway.
Security researcher
They are stealing security tools and license keys discovered on the targeted machine. We noticed them utilizing a virtual machine setup and conducting attack simulations to comprehend how to circumvent these products. The identified tools include:
- BitDefender
- CrowdStrike
- SentinelOne
- Sophos
It’s crucial that organizations meticulously track hosts incorporated into their tenant. And determine if a threat actor has installed an EDR using your license. To know if a threat actor installed an EDR with your license, some good indicators combination to search for anomalies are:
- BIOS Manufacturer
- Hostname
- Exit point
Nonetheless, this is highly dependent on your environment, look for anomalies in your context.
Detection avenue
In terms of tools, they use traditional penetration testing tools, as you can see in the figure below. However, the detection emphasis on these tools should operate under the assumption that the binaries will execute on a system devoid of Endpoint Detection and Response (EDR) systems. This is due to two factors: The threat actor possesses procedures to disable EDRs. They can also utilize their own machines to establish a connection with your infrastructure with a VPN client. We observed several VPN clients deployed on threat actor machines. Consequently, the detection focus ought to be on the behavior exhibited by these tools.
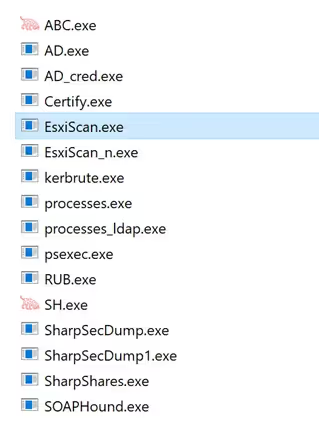
Figure 1 – Tools dump
APIs Access
Security automation gained popularity within the blue team. These automated systems leverage API keys which offer significant access to the security platform such as EDRs. They are often not as closely monitored by organizations as user credentials, based on our observations.
We’ve discovered threat actors utilizing API keys to interface with Endpoint Detection and Response (EDR) systems, which can go undetected for an extended period. Therefore, it’s crucial to implement detection rules for suspicious API key creation or usage. Fortunately, some EDR vendors provide excellent settings to mitigate these risks.
Recommendations
Threat actors, even at the cybercriminal level, actively research Endpoint Detection and Response (EDR) technologies. Given this, it’s crucial to assume that not only nation-state actors but also cybercriminals could potentially quickly disable your EDR agents.
Device hardening is essential, as is having detection mechanisms for suspiciously inactive agents. However, consider detection methods beyond EDRs. Identity Providers (IdPs), for instance, can be valuable allies in this regard.
API key usage must be closely monitored, as they can grant access levels that allow code execution on any machine within an organization and even disable your security solution. Instances of EDRs being exploited to deploy malware are likely to increase, even within leading EDR providers in the market.
Detection systems heavily focus on identifying known malicious behavior, and frameworks like MITRE have been instrumental in providing structure to this process. However, the most significant and advanced incident response cases we have worked on, were based on noticing anomalies within the network segment or organizational context. These detections are specific to each organization or network segment and may require some research to define, but they could potentially save you some days and a bad breach experience.
Deception can serve as an early warning system too. For example, leaving monitored API keys or agent installation scripts that trigger an alert when accessed can be an effective strategy.
Final note
If you require additional information, please don’t hesitate to reach out to your account executive. For non-Kudelski Security clients, in the event of an incident involving Blackbasta, please contact our incident response team directly.
Taha El Graini & KS Threat Research Team











































.avif)




.avif)















.webp)