Adversary Infrastructure and Indicators Behind the SAP NetWeaver 0-Day Exploitation
Adversary Infrastructure and Indicators Behind the SAP NetWeaver 0-Day Exploitation
On the 27th of March 2025, we’ve seen a previously unknown vulnerability (now tagged as CVE-2025-31324) in SAP NetWeaver Visual Composer being exploited in the wild, targeting exposed enterprise systems. The vulnerability allowed unauthenticated attackers to upload malicious JSP files and gain remote code execution, a critical risk for organizations running unpatched instances.
While technical details of the vulnerability have already been thoroughly documented elsewhere, this article focuses on a different aspect of the event: the observable indicators and adversary infrastructure used during the exploitation window.
Post-Exploitation via Webshells
After successful exploitation of the SAP NetWeaver Visual Composer vulnerability, attackers deployed JSP-based webshells to maintain access and issue follow-up commands. These webshells acted as a lightweight interface for remote interaction with the compromised systems.
Once established, the webshells were used to perform a range of standard post-exploitation tasks. These included:
- System and network reconnaissance, using commands like ipconfig, systeminfo, tasklist, and whoami to gather basic host information.
- Domain and user enumeration, with commands querying local and domain-level groups, trust relationships, and specific usernames.
- Outbound connectivity checks, notably via ping to external IP addresses (C2) to test infrastructure reachability.
- Payload staging, including PowerShell-based delivery of a Cobalt Strike beacon, observed in at least one instance.
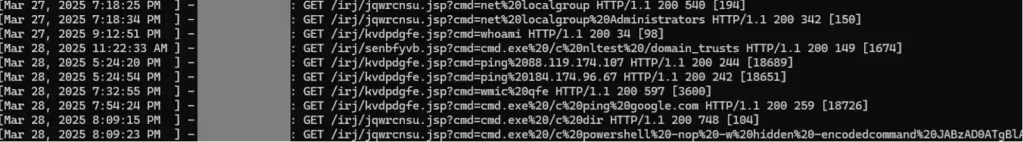
Figure 1- Sample of commands executed through the Webshells
Infrastructure Analysis
Two commands were issued to test infrastructure connectivity:
ping 184.174.96.67
ping 88.119.174.107These IP were identified as hosting active Cobalt Strike command-and-control servers at the time of the campaign.
- 184.174.96.67
The IP address 184.174.96.67 has been associated with the domain officetoolservices[.]com
The IP was clearly hosting a Cobalt Strike server, as evidenced by its HTTP status code 404 and the “Content-Length: 0”
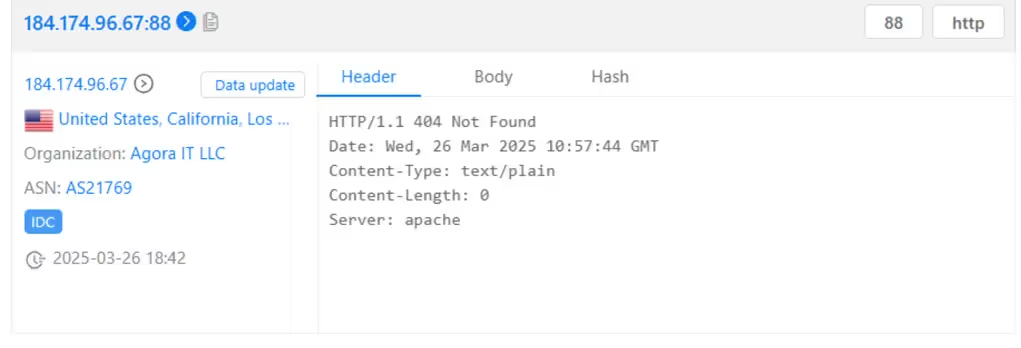
Figure 2- HTTP Response headers on port 88 taken from ZoomEye
In addition, at least four Cobalt Strike samples were using officetoolservices[.]com as their command-and-control (C2) domain:
52ed846c3b966539f851e79bba4172f0d460471012bb3933528367562ad6695c
89c272122477af854a51de4e220161d1c823a303151ebceb8788bb8ced2b7ba8
a8e44d7534d71b0671eb21400a1798296784af02124019b694b7e687405d7628
d2fa11395e93733d0957b8359faf19dd3c89bb044917e1488d74bd512c770c68
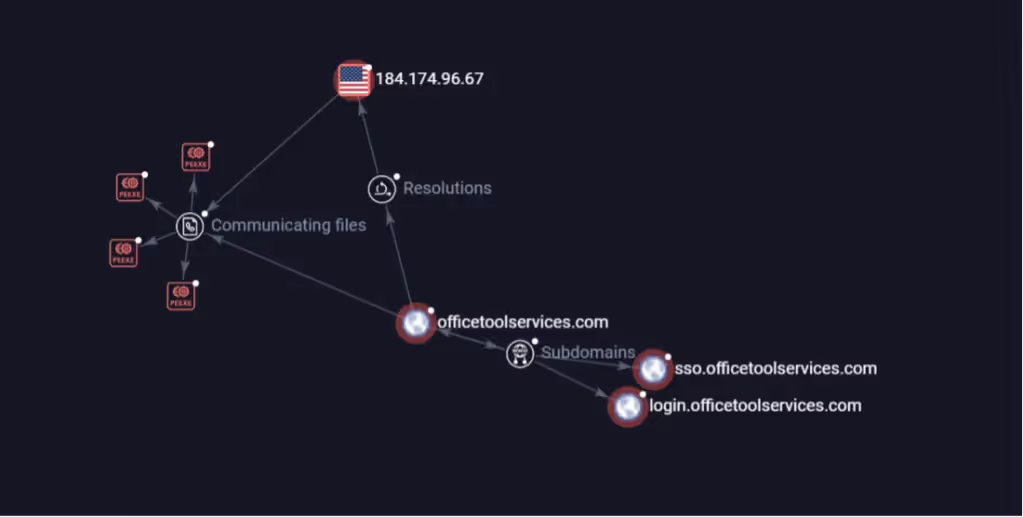
Figure 3- VT graph of 184.174.96.67
All four samples shared a compilation timestamp from early April, suggesting they were not part of the initial exploitation wave we observed at the end of March, but rather part of a second phase of activity, likely leveraging continued access or targeting additional victims using the same infrastructure.
- 88.119.174.107
The analysis of the IP address 88.119.174.107 confirms its part of the attack infrastructure. At least one Cobalt Strike beacon sample found on VirusTotal was configured to use this IP directly as its command-and-control (C2) endpoint.
The IP was also returning a HTTP response header “Server: golfe2” on multiple ports (8081,8082,6443,7443) combined with HTTP status code 404 and “Content-Length: 0”, confirming its running a CobaltStrike C2 Server.
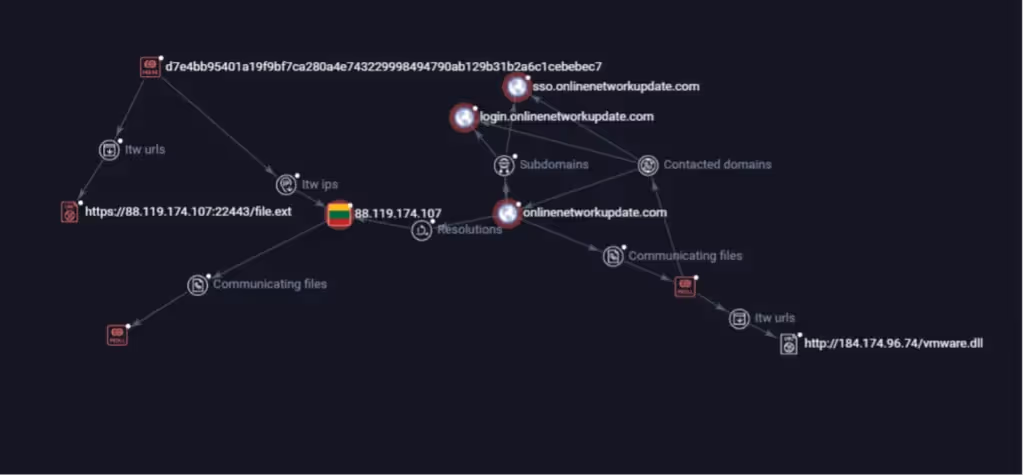
Figure 4- VT Graph of 88.119.174.107
In addition, a URL observed in the wild (https://88.119.174%5B.%5D107:22443/file.ext) was actively serving a Cobalt Strike payload during the exploitation timeframe. The file retrieved from this endpoint was identified with the following hash d7e4bb95401a19f9bf7ca280a4e743229998494790ab129b31b2a6c1cebebec7
- d7e4bb95401a19f9bf7ca280a4e743229998494790ab129b31b2a6c1cebebec7
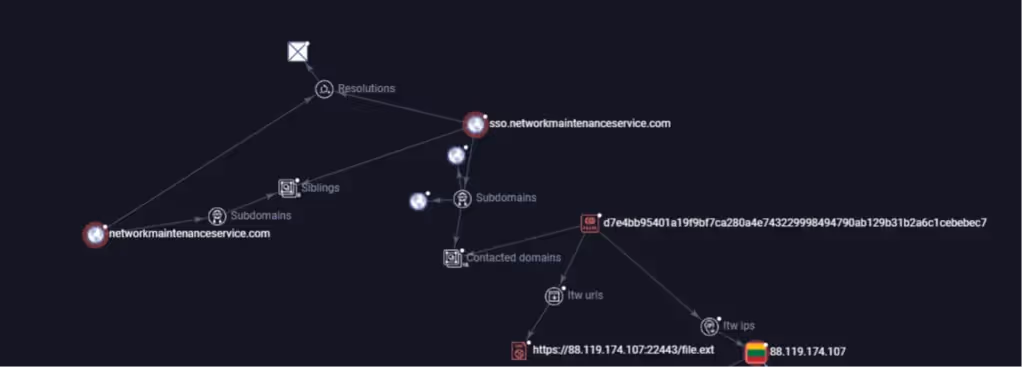
Figure 5- VT Graph of d7e4bb95401a19f9bf7ca280a4e743229998494790ab129b31b2a6c1cebebec7
Interestingly, although this beacon was delivered from 88.119.174.107, its internal configuration pointed to a different C2 domain: networkmaintenanceservice[.]com
This beacon is the same payload retrieved by a DNS cobalt stager we observed during the post-exploitation phase and had the following key configuration parameters:
{
"BeaconType": [
"Hybrid HTTP DNS"
],
"Port": 1,
"SleepTime": 23815,
"MaxGetSize": 2796804,
"Jitter": 41,
"MaxDNS": 253,
"C2Server": "www.networkmaintenanceservice.com,/sq,sso.networkmaintenanceservice.com,/sq,login.networkmaintenanceservice.com,/sq,signin.networkmaintenanceservice.com,/sq,profile.networkmaintenanceservice.com,/sq,store.networkmaintenanceservice.com,/sq",
"DNS_Idle": "253.58.253.29",
"DNS_Sleep": 133,
"HttpGet_Verb": "GET",
"HttpPost_Verb": "POST",
"HttpPostChunk": 0,
"Spawnto_x86": "%windir%\\syswow64\\runonce.exe",
"Spawnto_x64": "%windir%\\sysnative\\runonce.exe",
"CryptoScheme": 0,
"Proxy_Behavior": "Use IE settings",
"Watermark": 1357776117,
"bStageCleanup": "True",
"bCFGCaution": "False",
"KillDate": 0,
"bProcInject_StartRWX": "False",
"bProcInject_UseRWX": "False",
"bProcInject_MinAllocSize": 24330,
"ProcInject_PrependAppend_x86": [
"kJCQ",
"Empty"
],
"ProcInject_PrependAppend_x64": [
"kJCQ",
"Empty"
],
"ProcInject_Execute": [
"CreateThread",
"RtlCreateUserThread",
"CreateRemoteThread"
],
"ProcInject_AllocationMethod": "VirtualAllocEx",
"bUsesCookies": "True",
"HostHeader": ""
}- The watermark
A notable characteristic shared across all Cobalt Strike beacons observed from the previous links is the watermark 1357776117. In Cobalt Strike, the watermark is a unique identifier embedded in each beacon, typically tied to a specific license or build. While these IDs can be reused (especially in cracked or leaked versions of the tool) they often serve as useful correlation points across unrelated incidents.
Watermark 1357776117 has been previously associated with activity linked to both the BlackBasta ransomware group and the Qilin ransomware operation. Although watermark reuse complicates direct attribution, the appearance of this same identifier across all observed beacons suggests that the actors involved are likely ransomware-driven.
- Subdomains naming convention
Observation of the adversary’s infrastructure showed consistent naming conventions across multiple domains and subdomains. The attacker repeatedly used prefixes such as “sso.” and “login.” likely in an attempt to blend malicious traffic into legitimate enterprise communications.
Examples include:
- (login| sso).misctoolsupdate[.]com
- (login| sso).networkmaintenanceservice[.]com
- (login|sso).officetoolservices[.]com
- sso.leapsummergetis[.]com
The recurrence of these prefixes across unrelated domains suggests automated infrastructure generation, possibly using templated scripts or orchestration tooling to rapidly deploy new redirectors or C2 servers with plausible, enterprise-looking subdomains.
This campaign is a clear reminder that even ransomware groups now have access to zero-day vulnerabilities, once considered the exclusive domain of state-sponsored actors. Whether acquired through underground marketplaces, private exploit developers, or collaboration with initial access brokers, the use of a NetWeaver zero-day highlights how the ransomware ecosystem continues to evolve in both capability and reach.
The following list of indicators was extracted from observed activity related to the SAP NetWeaver exploitation campaign:
IP Addresses:
184.174.96[.]67
184.174.96[.]74
88.119.174[.]107
177.54.223[.]24
180.131.145[.]73
Domains:
officetoolservices[.]com
networkmaintenanceservice[.]com
misctoolsupdate[.]com
leapsummergetis[.]com
onlinenetworkupdate[.]com











































.avif)




.avif)















.webp)