Maximal Extractable Value (MEV): The Hidden Force Shaping Blockchain Security
Maximal Extractable Value (MEV) is one of the most fascinating and controversial economic forces shaping the future of blockchain ecosystems. Once a niche concept buried in technical discussions, MEV has quickly become a central issue for developers, traders, and anyone invested in the integrity of decentralized finance.
What Is Maximal Extractable Value?
MEV refers to the maximum value that can be extracted from block production beyond standard rewards and gas fees, primarily by reordering, inserting, or excluding transactions within a block.
In simple terms: those who control transaction ordering can profit from it. And profit they have. Since late 2020, validators have received more than $247 million in MEV-related payments, highlighting just how significant this hidden economy has become.
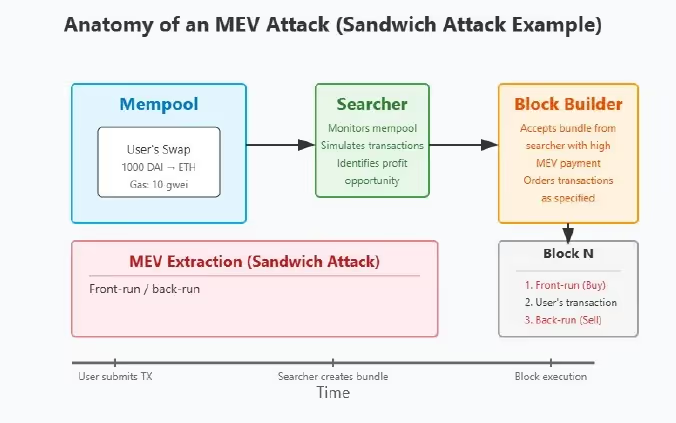
How MEV Attacks Work
Every Ethereum transaction first enters a mempool, waiting to be added to a block. Specialized actors, known as searchers (often automated bots), scour these pending transactions for opportunities to exploit. Their tactics include:
- Arbitrage: Taking advantage of price differences across decentralized exchanges.
- Liquidations: Triggering liquidations on lending platforms like Aave to pocket liquidation bonuses.
- Bundle Transactions: Executing carefully sequenced transaction bundles that only work if processed in the right order.
In this hyper-competitive environment, milliseconds matter. The result is a relentless technical arms race among searchers and validators.
Systemic Risks of MEV
While profitable for some, MEV introduces serious risks:
- Consensus Security Risks
In longest-chain consensus models, if MEV opportunities exceed block rewards, validators may be incentivized to reorganize the chain to capture profits. This undermines trust in consensus itself. - Centralization Pressure
Validators can cut out searchers and capture MEV directly. Over time, this fosters centralization, as a small group of validators or builders come to dominate block production. Already, just a handful of builders control the majority of Ethereum blocks, which raises real concerns about the erosion of decentralization.
Addressing the MEV Challenge
The blockchain community is experimenting with two major approaches to limit MEV’s damage.
Approach 1: Accept MEV, Minimize Harm
Since MEV cannot be eliminated entirely, this approach focuses on containing its risks.
Proposer-Builder Separation (PBS)
PBS removes gas-price auctions from the public mempool, creating a private off-chain marketplace where searchers compete for block space. This helps level the playing field and distribute MEV revenues more fairly.
MEV-Boost: Today’s PBS in Action
MEV-Boost splits block production into three roles:
- Builders: Assemble blocks from transactions and MEV bundles.
- Relays: Pick the most profitable block to forward to the proposer.
- Proposers: Approve the winning block without seeing transaction details.
This architecture prevents validators from stealing MEV while still allowing them to benefit from MEV payments.
Different relays have adopted distinct policies, which shape how MEV is distributed:
- Flashbots: Filters out OFAC-sanctioned addresses while maximizing validator payouts.
- BloXroute: Takes a no-censorship approach while maximizing validator payouts.
- UltraSound: Operates as a non-profit relay with no censorship.
Despite its benefits, MEV-Boost has limitations. Builder concentration remains high, with three builders currently responsible for 75 percent of all blocks. Most MEV profits flow to block proposers due to the first-price auction design, and MEV-Boost does not address cross-chain MEV opportunities, leaving room for arbitrage across networks.
SUAVE: The Next Step
Flashbots’ Single Unifying Auction for Value Expression (SUAVE) takes PBS further. It keeps transactions encrypted until signed while still enabling builders to compete. This requires cutting-edge cryptography, such as multiparty computation or secure enclaves, to balance privacy with availability.
Approach 2: Fair Transaction Ordering
Instead of accepting MEV, this approach tries to remove the ability to reorder transactions unfairly.
Time-Based Order-Fairness (Aequitas, Themis)
Transactions are ordered according to when most validators receive them. This reduces opportunities for manipulation, though it comes with technical challenges like Condorcet attacks.
Blind Order-Fairness
Using cryptographic commitments, transactions remain hidden until ordering is fixed. Two notable implementations are:
- Threshold Encryption: Validators jointly decrypt after block finalization.
- Timed Commitments: Transactions remain locked until after the block is confirmed.
Both approaches make it impossible to reorder transactions for profit once the block is sealed.
Builder Strategies: A Competitive Edge
Builders in the MEV-Boost ecosystem deploy advanced tactics to maximize profits:
- Submitting multiple block versions per slot.
- Incrementally raising bids as new MEV opportunities arise.
- Balancing the risk of waiting for bigger gains against missing the submission window.
This dynamic market ensures MEV remains both lucrative and highly contested.
Additional Protection Strategies
Beyond PBS and fair ordering, other defenses include:
- Private Transaction Pools: Shield trades from public mempools.
- Batch Auctions: Aggregate trades and execute at a uniform clearing price.
- TWAP Execution: Spread large trades over time to minimize exposure.
- Slippage Controls: Limit price manipulation during execution.
Strengthening Blockchain Fairness and Security
MEV sits at the intersection of economics, cryptography, and game theory. It may never be fully eliminated, but innovations such as Proposer-Builder Separation, SUAVE, and fair ordering mechanisms are steadily reducing its most harmful effects.
For developers and users alike, understanding MEV is essential. The way we address it today will shape not only the efficiency and fairness of blockchain but also its long-term decentralization.
At Kudelski Security, we help organizations navigate this evolving landscape. From assessing MEV vulnerabilities to designing defenses against manipulation, our blockchain security experts provide the guidance and solutions needed to build more resilient and trustworthy systems.
👉 Discover our Blockchain Security Services