Managed Detection and Response for Endpoint
MDR that delivers business value – get visibility and protection against elusive threats.

Effective Defense Against Today’s Most Sophisticated Threats
Attackers target endpoints because they provide an ample attack surface and immediate access to sensitive data. As working environments change, with cloud and remote work adoption, endpoint security technologies offer an effective defense in the fight against adversaries. Kudelski Security helps you optimize your technology investment by providing the human-led analysis, investigation, and response that make the real difference in effectively disrupting adversary activity and reducing risk.
Talk to UsMDR for Endpoints – Round the Clock Detection and Response
-

Extended Visibility
Analysis of detailed endpoint telemetry and alerts enable our analysts to identify and respond to threats – including the latest and most sophisticated – targeting your weakest link.
-

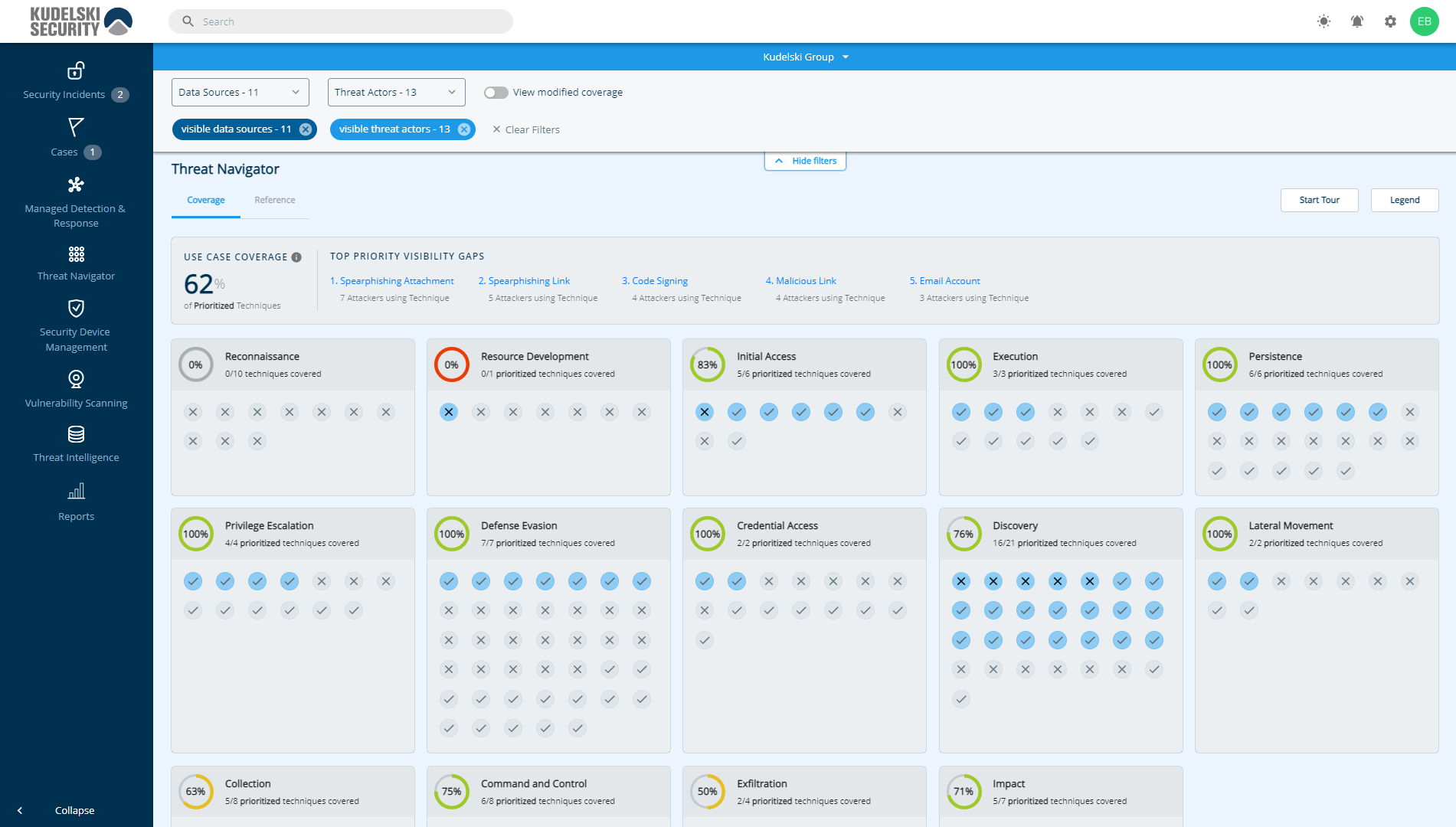
Effective Detection
Our MDR service for endpoints covers 85% of latest MITRE ATT&CK techniques, ensuring your protected from the threats that are most likely to disrupt your organization.
-

Rapid Response
Threats are neutralized in a matter of minutes – not days – thanks to a combination of proven methodologies, human-led intelligence, and industry-leading technologies.
-

Clear Remediation Guidance and Active Response Capabilities
We act as a force multiplier of your security team; our advice and hands-on support is always timely, intelligible, and actionable.
-

Improved Security Posture
Stay ahead of the curve, thanks to our evolving threat hunting practices and continuously improving threat intel.
Intelligence in Action
Kudelski Security MDR Services – Powered by the FusionDetect™ Platform
-
Collect
Aggregate, normalize and enrich security-relevant data across your environment. -
Analyze
Cross correlate & apply indicators of attack to map attacker behavior to MITRE ATT&CK techniques. -
Investigate
CFC analysts and threat hunters use FusionDetect™ to triage, investigate and validate identified threats & breaches. -
Respond
Automate initial response actions, accelerate escalation with clear remediation guidance & hands-on support. -
-
Collect
Aggregate, normalize and enrich security-relevant data across your environment. -
Analyze
Cross correlate & apply indicators of attack to map attacker behavior to MITRE ATT&CK techniques. -
Investigate
CFC analysts and threat hunters use FusionDetect™ to triage, investigate and validate identified threats & breaches. -
Respond
Automate initial response actions, accelerate escalation with clear remediation guidance & hands-on support. -
-

What the Analysts Say
“By 2025, 50% of organizations will be using MDR services for threat monitoring, detection and response functions that offer threat containment capabilities.”
Endpoint Security That Prevents Business Disruption
-
1
Endpoint telemetry collection, aggregation, and analysis – from your on-premises and cloud business environments
-
2
Proprietary Use Case Framework fully mapped to latest MITRE ATT&CK techniques
-
3
Industry-leading technologies for prevention, detection, deception, fully integrated into our FusionDetect™ platform
-
4
Continuous and retrospective threat hunting
-
5
Remediation recommendations and response on your team’s behalf
-
6
Award-winning MSS Portal with real-time dashboards and reporting on activity in your endpoints
Frequently Asked Questions
-
What is Kudelski Security’s approach to MDR for Endpoints?
Managed Detection and Response is a key part of our approach to disrupting the cyber kill chain. Security data collected is enriched with real-time threat intelligence, leveraging our FusionDetect™ platform, and analyzed for signs of malicious activity. Potential threats are instantly directed to experts within our Cyber Fusion Center (CFC) Threat Analysis team who triage alerts, perform in-depth investigations, and prioritize containment and remediation. This significantly reduces the risk of damaging, long-lasting data breaches by detecting anomalies and disrupting adversary movements in the early stages of an attack.
-
What are Attacker Deception Technologies?
Deception technology creates an alternative, invisible network environment seamlessly interwoven into the client’s network. As a result, attackers are deceived and slowed down, while you receive relevant, contextualized, remediation guidance to contain the breach and successfully maintain network protection. Leading-edge attacker deception technology is integrated with our CFC infrastructure to deliver a service that meets the security demands created by today’s advanced adversaries.
-
What endpoints can be secured with Kudelski Security’s MDR for Endpoints offering?
With Kudelski Security’s MDR for Endpoints offering, your most critical assets are secured. Any endpoint connected to your network – computers, laptops, servers, or cloud virtual machines – are covered and protected under our services.
Featured Resources
We're here to help.
Complete the form to talk with one of our security experts and learn how our award-winning security services can help you and your organization.