It’s no secret that cybercrime is on the rise with attacks happening more frequently and for higher and higher profits. Enhancing and advancing our threat detection and response capabilities has never been more crucial. But, as with most things in cybersecurity, that’s easier said than done. This article, drawing insights from a recent managed detection and response webinar, dives deep into what MITRE D3FEND is, the MITRE D3FEND framework, how it complements the MITRE ATT&CK framework, and you can use it to identify and close gaps in security visibility.
Contents
The Growing Importance of Cybersecurity Frameworks
In the face of rising cyber threats, understanding your security visibility priorities and any gaps you may have within that visibility is indispensable. Trying to get visibility into every single thing happening in your environment, however, is expensive, and for most organizations, impossible.
Fortunately, there are some valuable frameworks out there like MITRE ATT&CK and MITRE D3FEND that can help streamline threat detection capabilities. These are free tools that anyone can use to prioritize detection and close security visibility gaps effectively.
Read the blog: “Four Roadblocks to Faster Threat Detection & Response”
What is MITRE D3FEND?
MITRE D3FEND is a new project from MITRE, the creators of the well-known ATT&CK framework, that establishes relationships between attack techniques, countermeasures and digital artifacts. From the MITRE website:
D3FEND is a knowledge base, but more specifically a knowledge graph, of cybersecurity countermeasure techniques. In the simplest sense, it is a catalog of defensive cybersecurity techniques and their relationships to offensive/adversary techniques.
The D3FEND matrix
The D3FEND matrix categorizes countermeasure techniques into five stages of defense:
- Harden – application hardening, platform hardening, credential hardening, message hardening
- Detect – network traffic analysis, process analysis, file analysis, platform monitoring, identifier analysis, message analysis, user behavior analysis
- Isolate – network isolation, execution isolation
- Deceive – decoy environment, decoy object
- Evict – credential eviction, process eviction
Each countermeasure is mapped to related MITRE ATT&CK techniques as well as any artifacts generated by the associated ATT&CK techniques. For example, the MITRE ATT&CK initial access technique of “Spearphishing Attachment” (T1566.001) would produce a MITRE D3FEND artifact of “Inbound Internet Mail Traffic” (D3FEND Artifact):
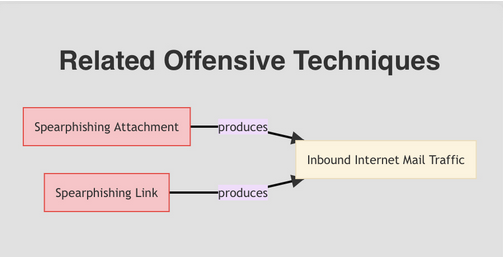
Figure 1. D3FEND inferred relationships for a spearphishing attack
MITRE D3FEND vs MITRE ATT&CK
D3FEND is a fairly new project that MITRE says is still in an experimental phase. We still find it incredibly valuable, especially when used in conjunction with the ATT&CK framework to prioritize security visibility requirements – and in the future, potentially even guide organizations in improving their resiliency by reducing attack surface.
MITRE ATT&CK – A knowledge base of attacker tactics and techniques
This is essentially a database that catalogs how attackers operate. It breaks down the tactics (broad categories of attack strategies) and techniques (specific ways attackers carry out tactics) used by cyber adversaries. The ATT&CK framework helps us understand the “how” of cyber attacks, mapping out the steps attackers might take. MITRE also provides some (somewhat limited) guidance around how to stop these attacks and data sources to leverage for detection and mitigation, but those really just scratch the surface and have been fairly focused on endpoint telemetry.
MITRE D3FEND – A knowledge base of cybersecurity countermeasure techniques
On the flip side, D3FEND focuses on defense. it’s a collection of methods designed to protect against attacks, making it harder for attackers to succeed. It does this by providing countermeasures that can be implemented to harden defenses and detect, isolate, deceive, and evict attackers from the environment.
The connective tissue between the two frameworks are the digital ‘clues’ that particular attack techniques generate. The techniques attackers use will produce some kind of digital evidence such as logs, network traffic, newly created or unauthorized user accounts, changes to email rules or application configurations, etc. Knowing which ‘clues’ to look for allows us to implement the appropriate security visibility to detect threat actors abusing those techniques. Additionally, understanding the sequence of an attack (the attack killchain) helps prioritize which defenses to put in place first, disrupting attackers before they can do significant damage.
Watch our recent webinar to learn how to strengthen your threat detection and response capabilities
A Step-by-Step Guide on How to Use MITRE frameworks to prioritize and close security visibility gaps
Step 1 – Define your cybersecurity threat model.
First things first, you’re going to need a threat model. Without this, you’ll end up spinning your wheels trying to stop every potential threat to your organization. Developing a threat model involves understanding potential threat actors, their objectives, and the MITRE ATT&CK techniques they might employ. This allows you to narrow in on the actual threat actors that may be targeting your organization based on factors like industry sector and geographic presence. At minimum, your threat model should accomplish the following five things:
At minimum, your threat model should accomplish the following five things:
- Provide you an understanding of threat actors targeting potentially targeting your organization
- Provide you an understanding of threat actor objectives (corporate espionage, financial gain, data theft, causing physical harm, etc) and a rough understanding of how threat actors attack (which techniques & tactics they use)
- Mapping ATT&CK techniques to your technology stack – and understanding which are applicable to your environment (do you use containers? If not, techniques related to Docker containers are not applicable)
- Understanding your attack surface
- Some details regarding remediation and risk reduction steps
Step 2 – Prioritize High Overlap Cyber-attack Techniques Based on the Killchain Stage, Using MITRE ATT&CK
With your threat model defined, you should have a good understanding of the types of threat actors targeting your organization, and you can start to identify where there is a high overlap of MITRE ATT&CK techniques these different threat actors use at each stage of the killchain.
Let’s say your threat model identifies APT28, more commonly known as Fancy Bear, as a threat actor that may be targeting your organization. You can reference the MITRE ATT&CK database to find the common techniques leveraged by APT28 to perform reconnaissance, gain initial access, establish persistence, etc.
Unless you’re very lucky, there’s not just one threat actor targeting your environment. So the next step is to cross-reference the techniques used by Fancy Bear with the techniques used by other threat actors to see if there are any techniques with really high overlap.
At Kudelski Security, we’ve developed a tool that helps speed up and visualize this cross-referencing step. In the example below, we can see that 42 of the threat actors we think are targeting our organization are leveraging Spearphishing Attachments to gain initial access. If we can prevent or detect a technique that’s very early on in the attack chain, then we have a much better chance of reducing the overall impact to the organization. For that reason, maybe Spearphishing Attachments should be our highest priority from a security visibility and detection perspective.
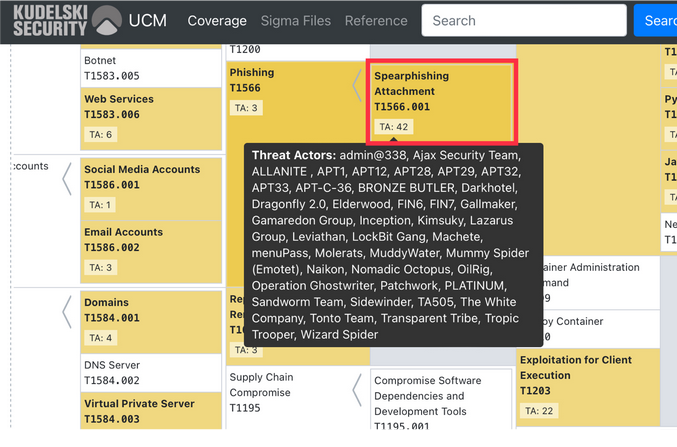
Once we’ve gotten really good at detecting Spearphishing Attachments, we may want to move on to detecting users clicking on Spearphishing Links, then maybe Drive-by Compromise and so on. If you can understand where attackers are succeeding and the techniques that they’re using, you can prioritize what your visibility should be.
Learn more about Kudelski Security’s managed threat detection and response capabilities
Step 3 – derstand Data Requirements for Technique Detection and Create a Data Checklist
Once you’ve got your list of offensive techniques prioritized, you need to understand the data that’s required to detect prioritized attack techniques.
This is usually where we see the most failures when it comes to threat detection. Either you’re collecting too much data, or you think you’re collecting everything you need to when in reality, really valuable logs (which may not be enabled by default) aren’t even turned on or being collected. This is often the case in standard Windows Active Directory Environments. We talk a lot more about this in our blog “Four Roadblocks to Faster Threat Detection & Response.”
Going back to our Spearphishing Attachment example, the MITRE database will tell us what data we need to collect in order to detect Spearphishing Attachments. According to MITRE, we should be collecting data related to:
- File creation
- Application log content
- Network traffic content
- Network traffic flow
The above list of data is a good example of the “Endpoint centric” nature of MITRE ATT&CK data sources. At Kudelski Security we’ve begun to expand on the data sources required for detection. As an example, to detect Spearphishing attachments we may also want data from email servers, email security gateways, and potentially things like Office 365 email audit logs.
This becomes our data checklist. If we’re already collecting this data or at least have the ability to collect it, then we know we have what we need to detect this specific technique. Your objective here is to better understand the data you’re sending to your security visibility tooling, identify any gaps you might have and then start closing those gaps.
You will have to balance how easy the data is to collect with how valuable the data is in detecting an attack. Of course, you’ll want to tackle any low hanging fruit. Enabling object access and change logs in Active Directory is pretty simple. Making a change across HTTP web server in your environment when you don’t have centralized configuration management capabilities is not.
Ultimately, you’ll have to decide if the juice is worth the squeeze. If a complicated change could give you better visibility into your overlapping techniques, it may be worth considering.
Step 4 – Prioritize Your Attack Mitigations, Using MITRE D3FEND
As the saying goes, the best offense is a good defense. With steps 1-3 complete, it’s time to think about how you can prevent these types of attacks, applying mitigations or countermeasures designed to stop specific techniques from evening working in the first place. Let’s look again at the MITRE D3FEND countermeasure database for the Spearphishing Attachment technique. You can see that there are 18 potential countermeasures that could either harden, detect, deceive or isolate the attack.
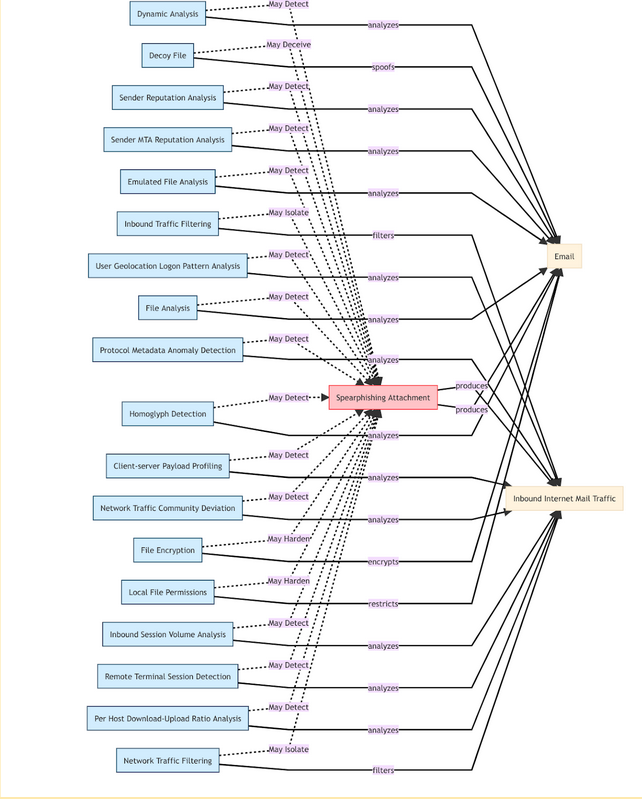
That’s a lot to take on at once, so we recommend prioritizing mitigations with these four strategies in mind:
- Mitigate techniques early in the killchain – the earlier in an attack campaign you mitigate, the less impact to your overall environment
- Prioritize based on value and ease of deployment – don’t tackle the hardest thing first, even if it’s the most valuable
- Leverage available audit modes and early adopters – Some mitigations may impact the way your users are used to working. Your job is to reduce risk while also ensuring your business can still function. Leverage “audit” modes of preventative tooling to understand the potential impact of a mitigation and identify things you need to whitelist.
- Consider user experience – build a process internally to handle exceptions to your mitigations
Get in Touch
We find both the MITRE ATT&CK and MITRE D3FEND frameworks really valuable and have incorporated them into our managed threat detection and response capabilities. Our team uses data from both in the internal tool we’ve built to help our team execute threat modeling and identify data requirements as outlined in this post. Though the tool is not a requirement for what we’re recommending, it can help streamline efforts.
If you’re interested in learning more or our managed detection and response capabilities in general, get in touch with our team or request a demo.