Maturity Is a Journey, Not a Destination
Several of the best CISOs I’ve worked with share a simple yet powerful goal: improve by 1% every day. It’s a mindset that fosters continuous progress without overwhelming teams— and it’s an essential approach in cybersecurity.
In cybersecurity, small, consistent improvements drive significant gains in overall security maturity. When each team member enhances their domain—whether by refining processes, improving documentation, increasing efficiency, or reducing complexity—these incremental changes compound into a more resilient, agile security program.
This philosophy isn’t unique to cybersecurity; it’s a core principle of business success. Like any critical function, security thrives on continuous improvement, ongoing refinement, and strategic evolution. The question is: how can CISOs and security teams make these daily improvements meaningful and impactful?
Avoiding the ‘All or Nothing’ Approach
I have also seen the opposite approach, where an organization or board suddenly decides that security is a top priority and expects all processes to mature fully within a short timeline, say, one year. This sets a hard and fast destination and without significant funding and resources, it is set up to fail. Maturity is not a box to check; it’s a process that unfolds over time.
Measuring Cybersecurity Maturity: From Reactive to Proactive
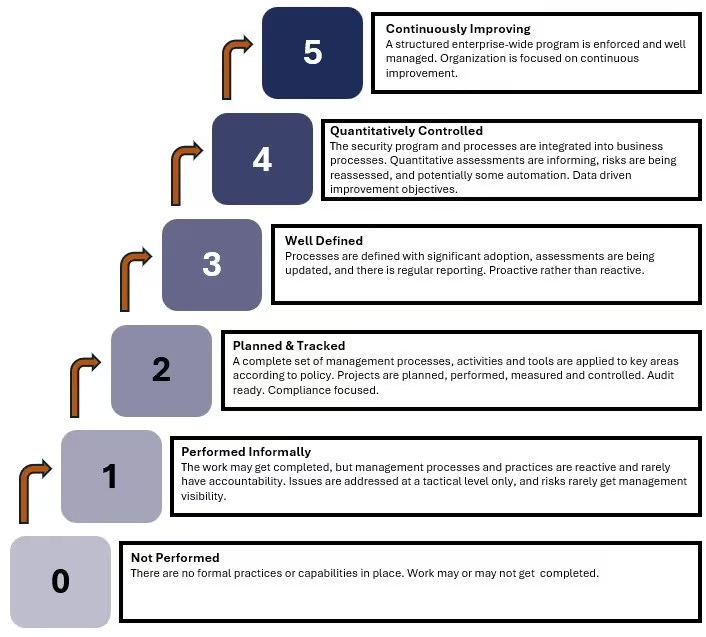
Kudelski Security utilizes a structured 0-5 maturity scale, which provides a clear roadmap for organizations looking to strengthen their security and operational processes:
- Level 0: No formal program development has begun.
- Level 1: Processes exist but are informal and reactive.
- Level 2: Processes are planned, documented, and systematically tracked.
- Level 3: Organizations operate proactively with well-defined, well-documented, consistently followed processes.
- Level 4: Leadership relies on documented metrics to drive strategic decisions.
- Level 5: A culture of continuous improvement is embedded, ensuring ongoing refinement and optimization.
A cybersecurity program can measure maturity at a control or process level. Objective – based cybersecurity frameworks such as NIST CSF v 2.0, are well – suited for maturity assessments. Conducting an initial current – state maturity assessment is critical to understanding where the program stands today.
Overcoming Obstacles in Your Cybersecurity Maturity Journey
One of the biggest challenges in cybersecurity maturity is resources – particularly people. Even the best-designed security strategy can falter if it relies too heavily on a single individual.
Securing leadership buy-in on the target maturity level is essential. Once that vision is established, the organization can take deliberate steps to move up the maturity scale. In many cases, a single strong resource can elevate a cybersecurity program to Level 2, but what happens when that person is promoted or leaves? Maturity often declines when key personnel change.
I’ve seen this scenario play out repeatedly with clients: “Bob used to run security operations, but since he left, everything has become ad hoc.” When security processes aren’t well-documented, widely understood, and consistently followed, the program’s maturity is tied to individuals rather than the organization as a whole.
So, what’s the solution? Build resilience into your cybersecurity framework. By establishing clear, repeatable, and well-documented processes, organizations can ensure that institutional knowledge doesn’t walk out the door when a key employee leaves. A mature cybersecurity program isn’t dependent on individuals—it’s built to sustain and evolve, no matter who’s on the team.
Building Resilience: A Lesson from Competitive BBQ
As a Kansas City guy, one of my favorite hobbies is cooking BBQ on the smoker. My friends and I have a BBQ team, entering into one or two competitions a year. But when we first started over 20 years ago, we weren’t exactly championship material. In the early days, only one of us really knew what he was doing.
Over time, we experimented, refined our techniques, and documented what worked (and what didn’t). We built repeatable processes, fine-tuned our recipes, and slowly improved. Eventually, we started winning ribbons—and even placed 6th overall one year at the Kansas State BBQ Championship. By maturity standards, we’d say our team is around level 3.
But you know who consistently outperforms us? The teams that compete 20 times a year. These are the teams that own BBQ restaurants on the side, meticulously track temperatures, analyze data and metrics, and constantly refine their approach.
Struggling With Cybersecurity Maturity? Start Small and Scale Up
Many of our clients are in this position today regarding Artificial Intelligence (AI). They want to do something but do not know what to do. Their employees are likely informally using AI for work items, putting the company at risk.
As my British co-worker likes to say, “We’re all rubbish when we start something.”
Organizations must start small and make incremental changes to increase maturity. Document leadership’s expectations in policies and standards, then communicate them to employees. Develop processes to implement AI use cases where the risk makes sense—then strive to improve those processes by 1% each day.
Prioritizing risk: The CISO’s Guide to Strategic Maturity Planning
Performing a risk assessment is crucial in determining where to focus cybersecurity efforts. Many frameworks, such as NIST CSF v2.0, now make risk management a core pillar of cybersecurity maturity.
Prioritizing risks based on potential risk reduction is critical. This approach allows teams to focus on the most pressing risks and improve them incrementally—rather than chasing the “fire of the day.” CISOs should use risk management as a driver of program maturity, aligning it with overall business risk.
Building a Culture of Continuous Cybersecurity Improvement
There are few organizations that can jump from zero to four on the maturity scale overnight—at least not without significant investment. Instead of unrealistic expectations, focus on steady, measurable progress. Encourage the team to embrace the 1% better everyday mindset, reinforcing a culture of continuous improvement that aligns with the CISO’s long-term strategy.
Successful organizations set clear, incremental targets—for example, increasing maturity by half a point every six months or one to one-and-a-half points per year. To stay on track, they develop detailed roadmaps with specific tasks designed to drive maturity forward step by step.
Regular check-ins with leadership ensure accountability and momentum, keeping the entire team focused on the bigger goal: building a security program that is not just mature but resilient, adaptable, and built for long-term success.
Small Steps, Big Wins: Cybersecurity Maturity Is Built Over Time
Cybersecurity is a journey, not a destination. Organizations must commit to a long-term mindset. The Cybersecurity teams must strive to get 1% better each day. Organizations must understand their current state, identify the most important risks, and develop project plans to methodically drive change.
Significant cybersecurity maturity does not happen overnight, and each organization must embrace the journey.
At Kudelski Security, our advisory services are designed to guide you every step of the way. Whether you're just starting out or striving for the next level of maturity, our experts provide the insights and tailored strategies needed to protect your organization in an evolving threat landscape.
Contact us today to see how we can help.



















